I A TO Z Solutions
PERIMETER FIREWALL

PERIMETER FIREWALL
A firewall is a crucial security measure that inspects and controls network traffic. It operates by enforcing predetermined security policies, which enable it to detect and block potentially harmful traffic. A well-configured firewall can significantly reduce the risk of unauthorized access, data breaches, and other security threats. Therefore, it is essential for organizations to implement a firewall as part of their security infrastructure to safeguard their network and data assets.
A perimeter firewall is a crucial security tool that serves to protect the boundary between a private network and a public network by preventing any potentially harmful data from accessing the network. While both data center firewalls and perimeter firewalls aim to safeguard an organization’s valuable assets, data center firewalls are specifically designed to protect virtual machines hosted within the organization’s data center.
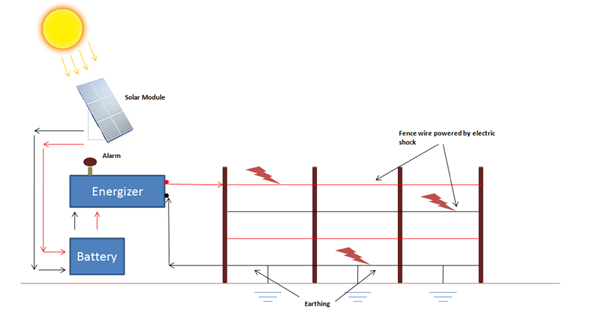
The network perimeter firewall, on the other hand, is a secure boundary that serves as the primary defense for a private network and other public networks, such as the Internet. The firewall is responsible for identifying and securing the network against any unwanted traffic, harmful code, and intrusion attempts. The network perimeter may include various components, such as border routers that direct traffic in and out of networks, firewalls that act as gatekeepers, intrusion detection systems that alert of suspicious activity, intrusion prevention systems that defend against attacks automatically, and demilitarized zones or screened subnets that provide extra security between external and internal networks by using logical screening routers to separate them.